Managing Third-Party Relationships: Effective Approaches to TPRM Risk and Compliance
Audit Board
JANUARY 11, 2023
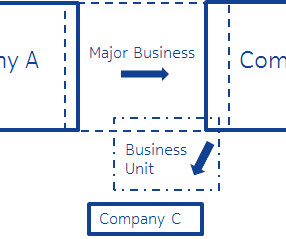
Benefits of Automating Third-Party Risk Management. The current environment of heightened third-party software attacks and subsequent legislative response is elevating third-party risk management (TPRM) as an organizational priority. The information management and automation benefits that. How to Respond.











































Let's personalize your content