Conducting Cybersecurity Risk Assessments Guide: The Complete Introduction
Audit Board
JANUARY 12, 2023
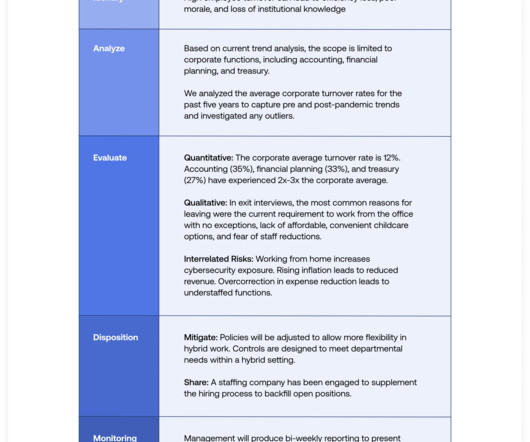
Cybersecurity risk assessments are a means for organizations to assess risks to their information assets and are a core requirement of most cybersecurity frameworks. It includes: A process flow for building and manage a cybersecurity risk management program. .









































Let's personalize your content