Subodh Mishra is Global Head of Communications at Institutional Shareholder Services (ISS) Inc. This post is based on an ISS Corporate Solutions memorandum by Liam Hardy, Senior Associate, ISS Corporate Solutions.
Digital technology impacts businesses in myriad ways. The internet enhances the interconnectedness of people, systems, and processes, leading to added value for the products and services that make up economic activity. At the same time, this dependency exposes corporate issuers to an increasing amount of information security-related risk, raising alarm among stakeholders. Strong oversight to help mitigate this risk is becoming critical to the health of corporations and thus is viewed increasingly as a key governance issue. Such oversight should be structural and rooted in a company’s leadership and organizational design, including the board. While disclosure trends suggest that businesses are closing the gap with expectations, many companies may find areas for improvement.
Good information security oversight should seek to reduce a company’s potential risk of harmful economic outcomes. Cybersecurity breaches can cause widespread damage to operations, resulting in significant costs and damages.[1] The heightened threat of a breach has spurred greater scrutiny of companies’ programs and practices from proxy advisors, regulators, and investors. As a result, companies are building into their disclosures more comprehensive reporting of mitigation efforts. The Securities and Exchange Commission (SEC) announced new rules in July 2023, requiring public companies to disclose their information security risk management strategies and governance practices annually, and quickly report any material cybersecurity incidents (see ISS Insights: SEC Cybersecurity Rules Set New Hurdles for Public Companies).[2] As these mandates come into effect, businesses should consider not only how to comply with the new rules, but also how they can best demonstrate robust information security governance.
DISCLOSING A CYBERSECURITY APPROACH
Companies expand efforts to report programs and strategies
In advance of the SEC rules, companies have been making a concerted effort to signal to stakeholders that they have an effective approach to managing cybersecurity threats. Nearly all companies in the Russell 3000 provide disclosures that reveal at least a general approach to information security risk mitigation. Furthermore, more than half of those include detailed disclosure of the information security risks, as well as strategies or plans to mitigate them, suggesting a “clear” approach – for example, adoption or certification of the ISO 27005. When confined to just the S&P 500, more than 80% of companies include such details regarding both the risks and methods used for mitigation. Firms that do not discuss their cybersecurity approach in detail may be increasingly viewed as lagging the market, as more companies seek to provide greater visibility into their risk mitigation strategies to investors.
Companies are now expected at a minimum to have an information security training program for employees to raise awareness of threats and blunt their impact. Breaches may occur at any step in the value chain, and alerting employees to the potential for human error, weak credentials, or malicious actors will likely provide one of the most effective methods for prevention. Rigorous programs executed regularly may deter costly breaches from occurring in the first place. Firms may also emphasize the robustness of their program by indicating whether they include specialized training offered for employees, executives, or directors.
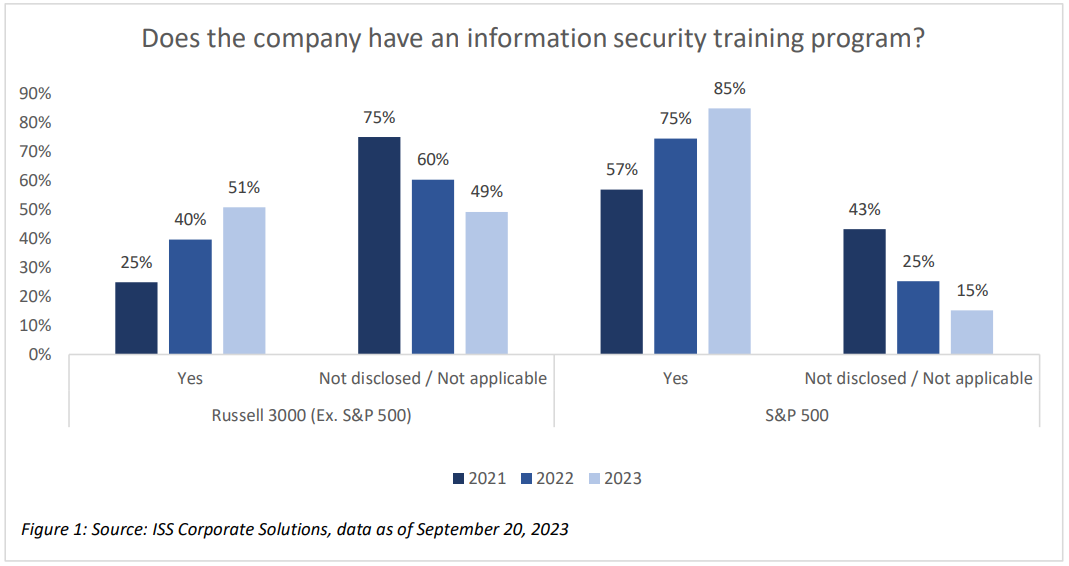
More companies are choosing to indicate the presence of a training program with nearly 85% of the S&P 500 and half of the remaining Russell 3000 making such disclosures. This represents a significant increase over the past two years (nearly 55% increase for the S&P 500 and 100% for the Russell 3000 (Ex. S&P500)), with more companies choosing to disclose details of their training programs in addition to implementing new ones.
CONSISTENT GROWTH IN COMPANY TRAINING PROGRAM FREQUENCY
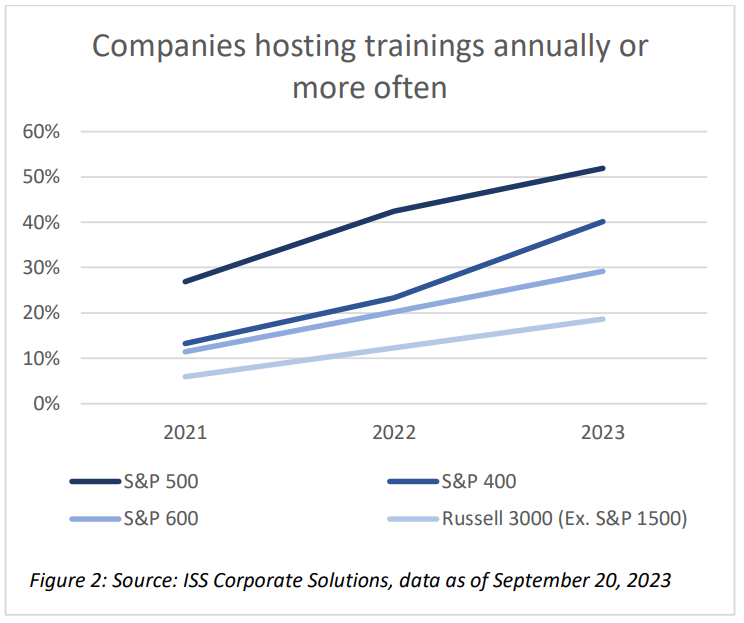
There is a consistent growth in all indices of companies hosting information security trainings at least annually, and S&P 500 companies outperform with more than half delivering these programs at least on an annual basis.
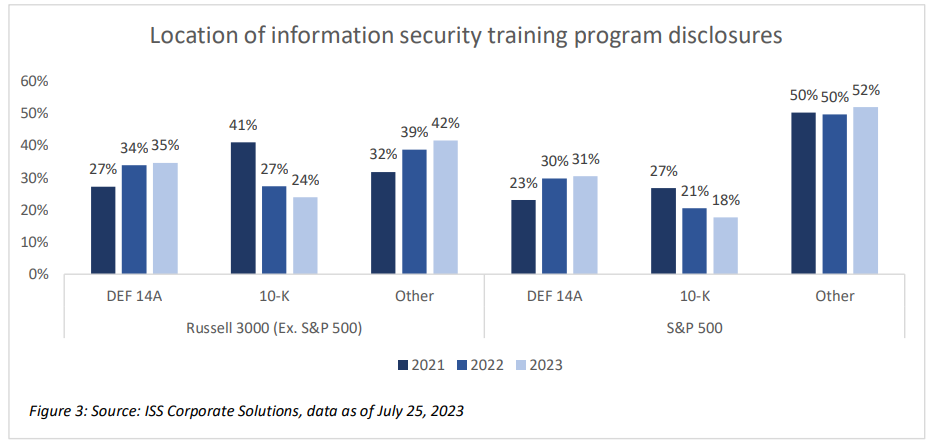
The location of these disclosures is almost evenly split between companies’ proxy statements (DEF 14A), annual reports (10-K), and other public disclosures, such as corporate sustainability reports or company websites. However, fewer have appeared in annual reports over the past two years, in favor of proxy statements or other places.
The presence of information security risk insurance is another indicator that a company has a program to protect itself from cybersecurity risks.[3] However, companies may be less inclined to report this. A common perception remains that disclosure of risk insurance may telegraph vulnerability to cybercriminals and make the company a greater target. In fact, having such insurance typically implies that the carrier’s minimum risk standards have been met, implying a lower level of risk. While no anecdotal evidence suggests that companies are impacted for revealing the existence of risk insurance, this disclosure may be useful for stakeholders since obtaining insurance suggests the company has taken steps to reallocate its financial risks if a costly breach occurs.
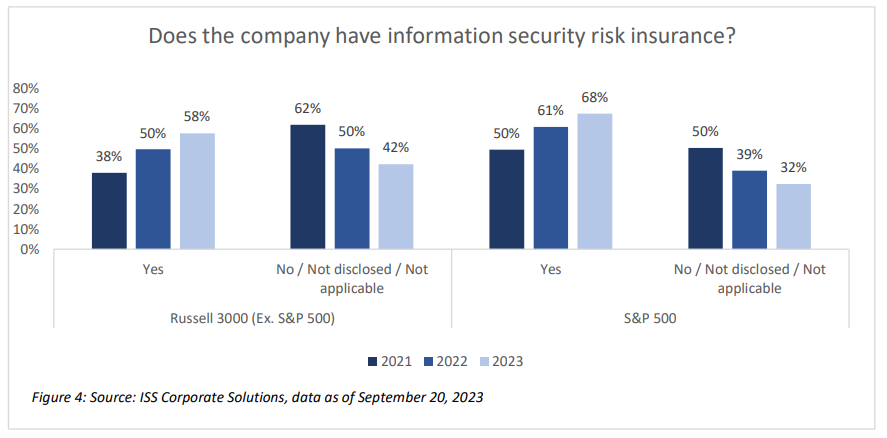
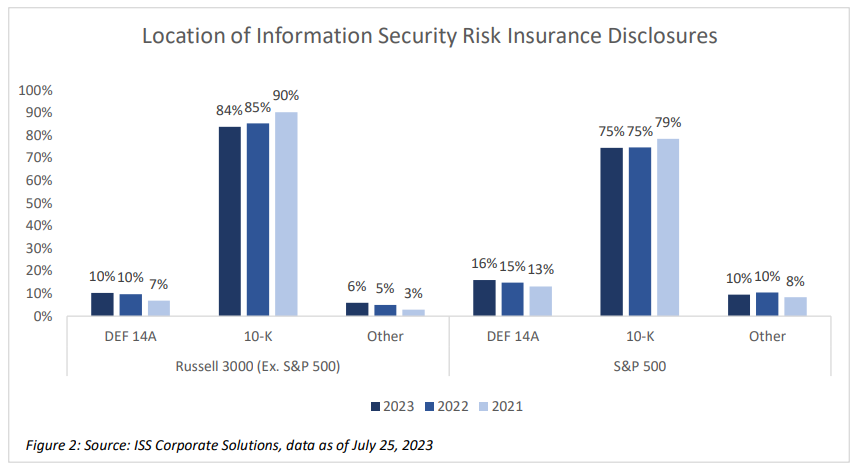
Nearly 67% of S&P 500 companies and 57% of Russell 3000 (Ex. S&P500) companies had disclosed that they have information security risk insurance as of September, an increase in disclosure over the past two years. Most companies remain underinsured, given the scale of exposure, and insurers face unique challenges in meeting industry demand. Nevertheless, as with company training programs, more companies are disclosing the presence of risk insurance or adding new policies. Such disclosures are more common within a company’s annual report (10-K) with nearly 80% of the S&P 500 and nearly 90% of Russell 3000 (Ex S&P500) companies disclosing their information security risk insurance policies there rather than the proxy statement (DEF 14A) or other places.
DIRECTOR EXPERTISE
Issuers seek to demonstrate information security competence and accountability on the board
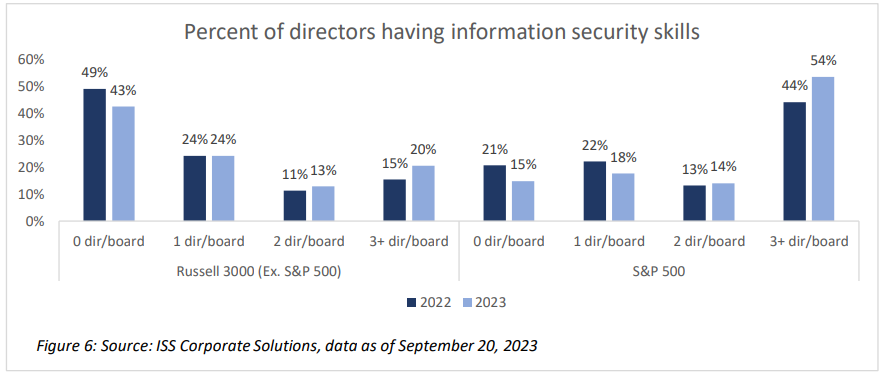
Cybersecurity risk oversight has increasingly become a board-level concern, and more companies are seeking to demonstrate that their directors have the necessary expertise to confront the challenge. The final version of the SEC Rules excluded an anticipated requirement that boards explicitly disclose the cyber-related expertise of board members. Regardless of companies’ willingness to disclose directors’ cyber expertise, many investors recognize that directors have a duty to exercise diligence in information security oversight for the benefit of shareholders. Having directors with relevant skills signals to investors that the board has the necessary expertise to effectively oversee cybersecurity risks. Directors with information security expertise are more common among larger companies with more than half of S&P 500 companies having at least three directors with the relevant expertise[4]. Directors with such expertise are less commonly found at smaller companies, though. Among Russell 3000 (Ex. S&P500) companies, more than 40% do not have any directors with cybersecurity expertise, and only about 20% of companies have more than three directors with the skills.
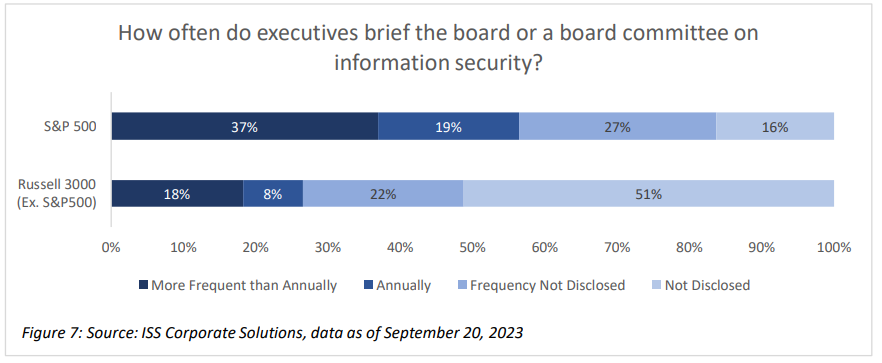
Boards and management are expected to coordinate more than ever on cybersecurity, and along with enhancing expertise, companies may also need to close the communication gap that frequently exists between directors and executives.[5] While most companies in the S&P 500 brief either the entire board or a committee on information security measures annually or more frequently, more than half of companies in the rest of the Russell 3000 do not disclose whether such briefings take place. Proactive boards that hold regular communications with their Chief Information Security Officer and other executives with responsibility will find themselves in a better position to provide effective information security oversight.
CYBERSECURITY BREACHES
More companies reporting incidents, with a greater increase in those having non-material breaches
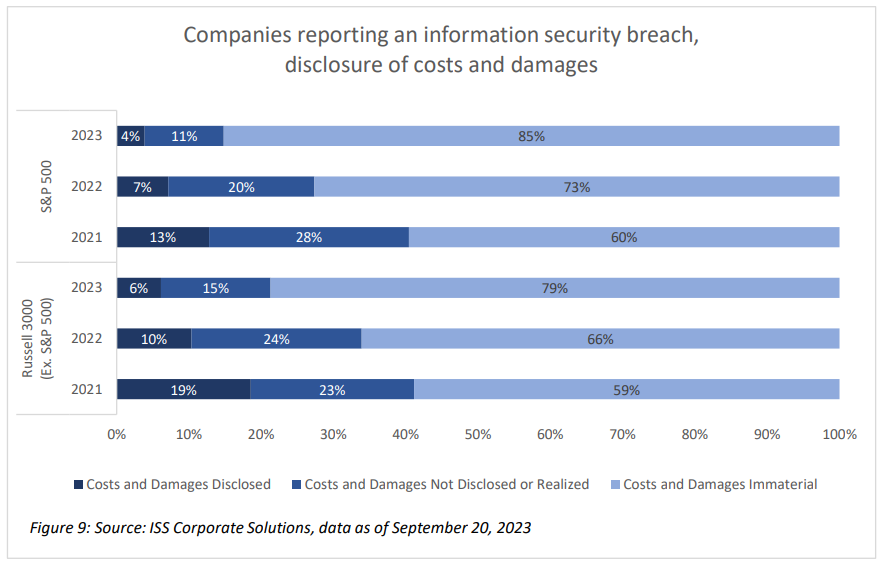
Companies that experience a cybersecurity breach must move quickly to disclose this information to comply with the new SEC rules, generally within four days. While other indicators provide stakeholders with information on a company’s posture for potential information security risks, disclosure of a breach provides investors with information necessary to assess the impact. Even prior to the new SEC rules, which take effect on Dec. 5, the number of companies disclosing a breach was increasing. More than 30% of S&P 500 companies and nearly 20% of the remaining Russell 3000 disclosed a breach – either material or immaterial – within the past three years. However, the majority of firms did not indicate whether any breach occurred or not, with nearly 56% of S&P 500 and nearly 70% of Russell 3000 (Ex. S&P500) being silent on security breaches as of September 2023. Of course, it is unclear whether the lack of disclosure is due to the lack of breach events at these firms, but the SEC rules will likely lead to more complete and accurate disclosures, creating better comparability among companies and enabling investors to assess the scope and impact of breach incidents.
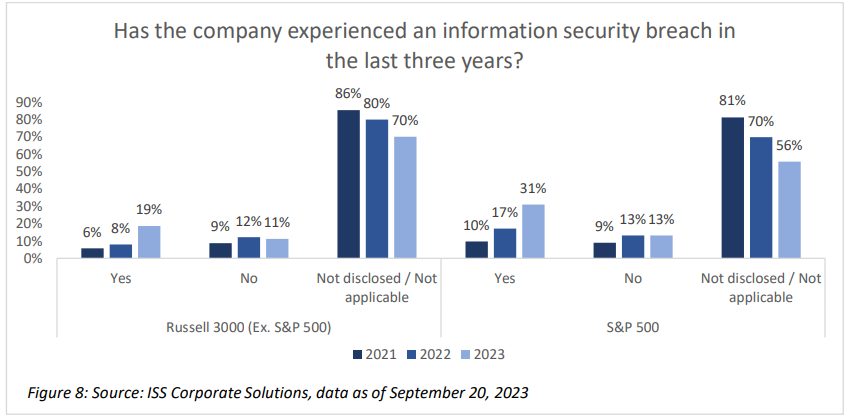
Among the companies disclosing an information security breach, the number of incidents where the costs and damages were not materially disruptive has increased as a proportion of the total. The number of companies reporting a breach that included costs and damages has held steady over the past three years. However, more companies are disclosing breach activity with no material impact on the business (or rather that there were no material breaches, leaving open the possibility that there may have been immaterial ones). As of September, nearly 85% of incidents reported among the S&P 500 and nearly 80% of those reported in the Russell 3000 (Ex. S&P500) were described as immaterial.
EXECUTIVE COMPENSATION
Few companies incorporate cybersecurity metrics into incentive programs
Executive compensation has so far seen little overlap with information security readiness, as businesses more commonly rely on financial and other strategic objectives to evaluate and reward performance. Nevertheless, a handful of companies explicitly incorporate cybersecurity-related objectives in either annual or long-term incentive programs for executives. These include at least 16 companies in the S&P 500 and 22 in the remainder of the Russell 3000. Such cybersecurity metrics may be represented as a weighted metric on a scorecard (for example, the internal report rate for a phishing program) or included as one of stated strategic goals for executives. As threats proliferate, companies that are forward looking on information security may consider whether such goals are appropriate based on their industry, business model, executive responsibilities, and specific programs.
1 Clare, Doug. (September 22, 2023). MGM Cyber Breach: Rethinking the Odds. ISS Insights. Retrieved from URL: https://insights.issgovernance.com/posts/mgm-cyber-breach-rethinking-the-odds/ (go back)
2 Clare, Doug. (July 28, 2023). ISS Insights. SEC Cybersecurity Rules Set New Hurdles for Public Companies. Retrieved from URL: https://www.isscorporatesolutions.com/library/sec-cybersecurity-rules-set-new-hurdles-for-public-companies/ (go back)
3 Johansmeyer, Tom. (January 11, 2021). Harvard Business Review. Cybersecurity Insurance Has a Big Problem. Retrieved from URL: https://hbr.org/2021/01/cybersecurity-insurance-has-a-big-problem#The%20Short-Term%20Problem (go back)
4This may include directors with current or prior experience at a cybersecurity firm, a current or prior cyber-related role such as Chief Information Security Officer or similar, an information security-related certification, or explicit disclosure of the skill.(go back)
5 Stupp, Catherine and Nash, Kim. (January 3, 2023). Wall Street Journal. Ukraine War and Upcoming SEC Rules Push Boards to Sharpen Cyber Oversight. Retrieved from URL: https://www.wsj.com/articles/ukraine-war-and-upcoming-secrules-push-boards-to-sharpen-cyber-oversight-11671723827?st=cfy7fystw4kwrzn&reflink=article_email_share (go back)
 Print
Print