Alex Holt is Global Head of Technology, Media & Telecommunications, Mark Gibson is U.S. National Sector Leader of Technology, Media & Telecommunications, and Vijay Jajoo is Principal of Cyber Security Services, at KPMG LLP. This post is based on their KPMG memorandum.
Tech company leaders name cyber security as both the greatest threat and greatest operational priority. In response, they are investing in skills, culture, and technology to build cyber resiliency, accelerate digital and business model transformation, and foster stakeholder trust.
Technology companies continue to provide the products and services that have powered digital transformation throughout the COVID-19 pandemic and allowed the wheels of global industry to keep turning. Yet this digital acceleration has also caused an explosion in the number of potential cyber vulnerability points due to an immediately virtual workforce, increased cloud adoption, hastily reworked supply chains, and new business partnerships. The rapid integration of new technologies also created an avalanche of new data to be stored and protected.
While some of these trends were already underway, the pandemic dramatically accelerated them. Technology companies were forced to react quickly like all others. In this new reality, technology company CEOs rank cyber risk as the greatest threat to their organization’s growth over the next three years, higher than even supply chain disruption, climate change, or talent risk.
They also cite cyber security resiliency as their most important operational priority. Additional research indicates the average cost of a data breach involving one million compromised records is $52 million, and the cost escalates from there. When more than 50 million records are compromised, the average cost of the breach is $401 million.
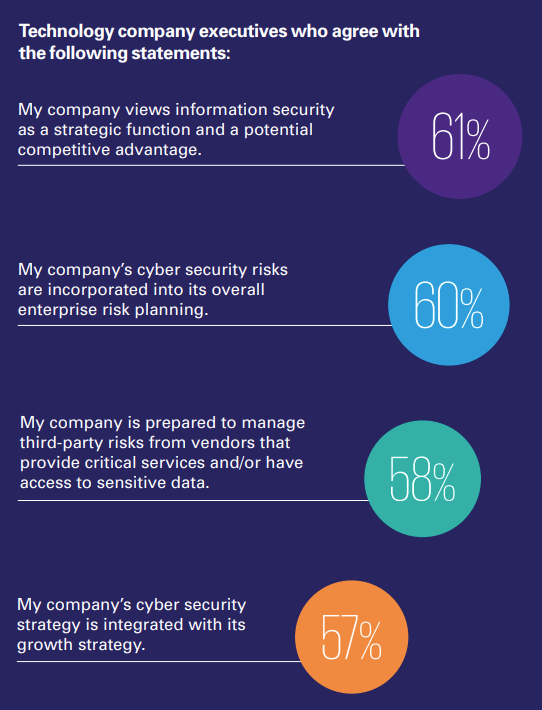
Yet technology company leaders also recognize that opportunity exists. A strong cyber strategy enables a company to maximize the fullest benefits of digital transformation to quickly grow the business while knowing risks are managed. Sixty-one percent actually view their information security as a competitive advantage. More than half (57 percent) say their cyber security strategy is integrated with their growth strategy.
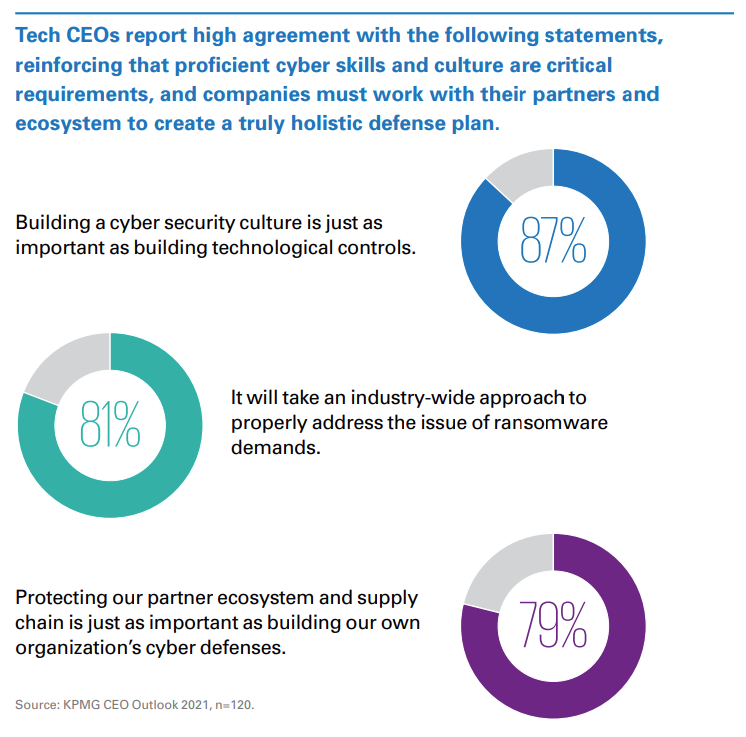
The vast majority (77 percent) of tech CEOs believe a strong cyber strategy is critical to engendering stakeholder trust.1 A strong cyber strategy incorporates both people and technology. The ongoing shortage of cyber talent dictates that all employees across all functions improve their cyber proficiency. Chief Information Security Officers (CISOs) are also stepping up—expanding their role to increase collaboration and their influence with other business unit leaders. From a technology standpoint, company leaders are increasing their investments in a variety of solutions to enhance organizational safeguards.
Cyber security has expanded beyond its traditional risk management and compliance focus to become a competitive advantage that enables stakeholder trust and fosters organizational resiliency. It is no longer exclusively an IT issue—it is a strategic priority that needs to be embedded throughout an organization’s culture, technology, and operations.
Key findings
KPMG canvassed opinions on cyber security issues from tech company CEOs and senior executives in two separate global studies: the Technology Industry Survey and the CEO Outlook. Key findings include the following:
Investing in skills and technology
Building a human firewall
Technology CEOs recognize the threat environment changes constantly, and sophisticated solutions can be the foundation of a cyber security program.
However, technology cannot protect everything. It needs to be reinforced by human behavior. Many studies show that a large percentage of reported breaches include some element of human error. That makes it critical for businesses to develop and maintain a comprehensive cyber security strategy that incorporates skilling the workforce.
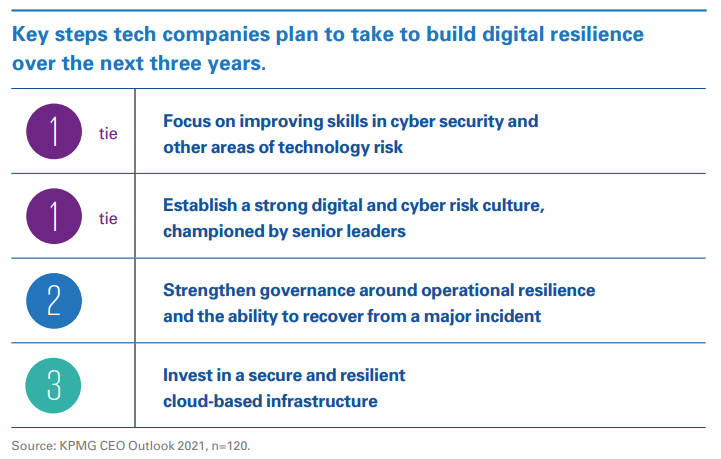
Human firewalling allows companies to move beyond cyber awareness and build an integrated, holistic approach to employee communication and training around cyber security—elevating employee behavior from a conscious choice to an ingrained habit. Tech CEOs recognize this and cite skills and culture as the top actions they are taking to build cyber and digital resiliency over the next three years.
Tech companies are also part of a complex ecosystem of suppliers and partners, tied together through shared data and shared services. Traditional contracts and liability models seem ill-suited to this rapidly evolving supply chain. The cyber education, behavior, and culture within these partners must change too in order to bring security to all parties.
Cyber security requires a technological village
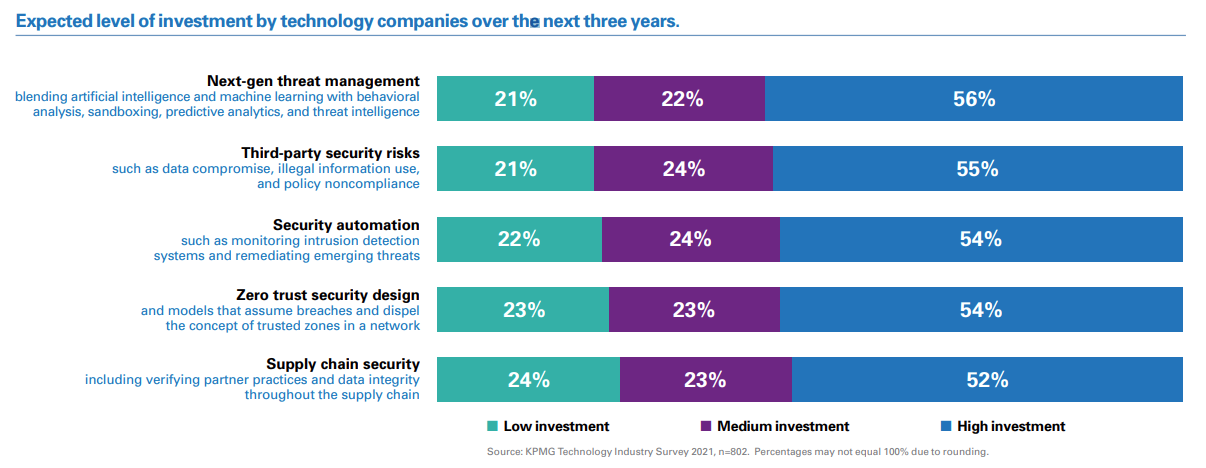
Enterprises have long recognized that one technology or process is unable to mitigate cyber risk by itself. They need to invest continually and broadly to identify emerging threats, improve the organization’s response capabilities, and increase efficiency within their security function and business units. Tech leaders also feel that while cyber tools are necessary to enable enterprise success, they cannot be so intrusive that they hinder operational efficiency or growth.
When asked about specific security investments, tech firm executives confirmed they plan high investment across multiple areas over the next three years. Investment in automation, specifically, can reduce the manual workload, ease skill shortages, foster greater efficiency, and help meet growing compliance requirements in a consistent and repeatable way. It can also help embed security and improve the user experience, as well as reduce the time to respond to a major cyber incident.
We are heading toward a further hyperconnected future in which the Internet of Things (IoT) and 5G networking will massively increase efficiency and enable radically different business models. But this also opens up organizations to new attack vectors and privacy concerns—demanding a shift to new, data-centric security models such as zero trust. Another KPMG study—The Data Imperative—found that 44 percent of respondents believe an effective data strategy would have a high impact in improving cyber security.
Cyber investment yields optimism
Technology company leaders are optimistic overall about the state of their information security function, as well as the degree to which it is integrated with their broader risk management efforts, third-party partnerships, and business unit leadership. Nearly three-quarters (74 percent) of tech CEOs say they are prepared for a future cyber attack, compared to 58 percent across all industries.
They believe their increased investments and focus have yielded sufficient enterprise capabilities to largely mitigate cyber risks. This confidence, and the investment required to achieve it, is necessary because 77 percent of tech CEOs also believe that a strong cyber strategy is critical to engendering trust with key stakeholders.
The redefined CISO
With technology companies blending on-site and remote workers, IoT devices, third-party partners, and service providers in dynamic teams and ecosystems, the CISO is taking a broader role in not only maintaining cyber security, but also overall organizational resilience.
As threats and regulatory expectations evolve, CISOs are taking on increased responsibilities and building relationships with a wide range of functions and business unit leaders. The CISO’s role is moving beyond “protect and detect” to enabling the business to get up and running quickly after an incident, as well as helping the CEO preserve trust with customers, suppliers, regulators, and other stakeholders.
CISOs are interacting more with CEOs and boards, providing consistent updates on emerging threats and mitigation efforts, while maintaining their traditional relationships with Chief Technology Officers and Chief Information Officers. They are helping to integrate security into governance and management processes, education, and awareness, plus establishing the right mix of corporate and personal incentives to do the right thing.
CISOs are also leveraging this opportunity to enhance organizational resilience by working to embed security- and privacy-focused design principles throughout their companies’ digital infrastructures. This expanded scope allows organizations to enhance their ability to mitigate cyber, regulatory, and business risks more effectively.
Seven steps that CISOs should consider to enhance their role.
- Speak the language of the board by thinking in terms of customers, revenue, costs, and return on investment.
- Focus on operational resilience like keeping the lights on and getting back to normal quickly following a crisis.
- Invest time in building a network within your organization, visiting different functions, learning how they operate and gaining trust.
- Think about shaping the workforce to the cyber needs of the business—as opposed to permanent roles and structures. Consider the ratio of employees to contractors and gig workers.
- Build a business case for automation, reflecting the efficiencies it brings and the value added from workers who are freed up for higher-level tasks.
- Work out what zero trust means for your business and see this as an ongoing philosophy rather than a one-off program.
- Find ways to reach out to peers in your sector, by joining existing industry bodies or forming less formal groups.
Key considerations for company leaders in 2022
Expand the strategic security conversation
Change the conversation from cost and speed to effective security to help deliver enhanced business value and user experience.
Develop critical talent and skill sets
Transform the cyber security team from enforcers to influencers.
Adapt security for the cloud
Enhance cloud security through automation—from deployment and monitoring to remediation.
Place identity at the heart of zero trust
Put identity and access management and zero trust to work in today’s hyperconnected workplace.
Exploit security automation
Gain a competitive advantage through smart deployment of security automation.
Protect the privacy frontier
Move to a multidisciplinary approach to privacy risk management that embeds privacy and security by design.
Secure beyond the boundaries
Protect the organization by encouraging the broader supply chain to be cyber secure.
Reframe the cyber resilience conversation
Broaden the ability to sustain operations, recover rapidly, and mitigate the consequences when a cyber attack occurs.
The complete publication, including footnotes, is available here.
 Print
Print